Potential applications for zero-knowledge include, but are not limited to:
- Inter-bank transfer systems (see a research paper by Narula et al.)
- Privacy-focused management of digital assets (see a proof of concept by J.P. Morgan and zCash)
- KYC (see a proof of concept by ING)
- Self-sovereign identity (see an attribute-based credentials EU project)
- Voting (see a proxy voting prototype by Russian National Security Depository)
Another application for zero-knowledge proofs is helping blockchains scale. ZKPs allow for the “compressing” of computations for blockchain transactions without sacrificing security.
In this article, we describe how zero-knowledge (specifically, Bulletproofs) can be applied to build a privacy-focused service using Bitfury’s Exonum platform.

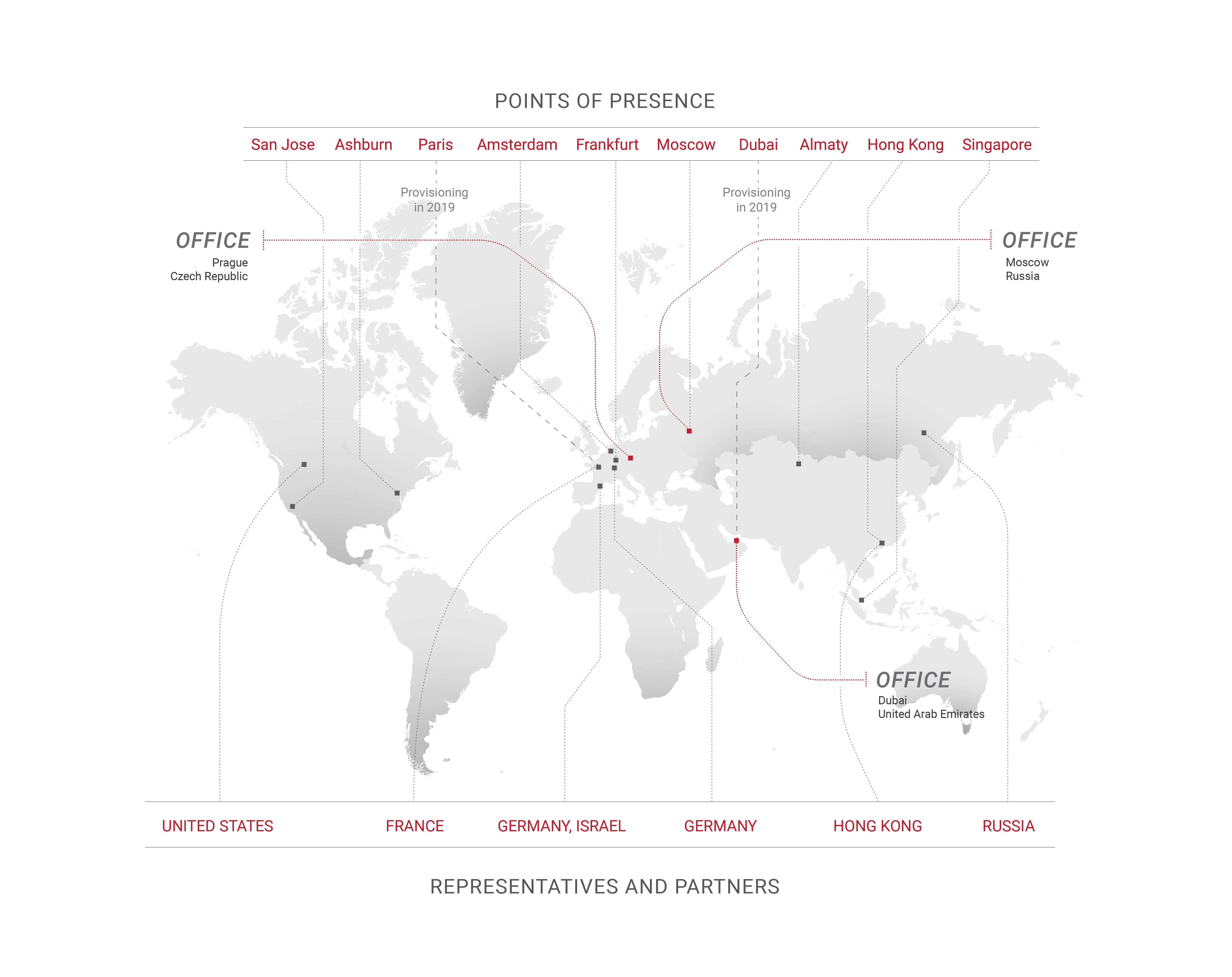





 This article contains a brief squeeze from my own experience and that of my colleagues, with whom I had been fighting incidents day and night. And many incidents would never have occurred if all these microservices that we love so much were written at least a little more carefully.
This article contains a brief squeeze from my own experience and that of my colleagues, with whom I had been fighting incidents day and night. And many incidents would never have occurred if all these microservices that we love so much were written at least a little more carefully.
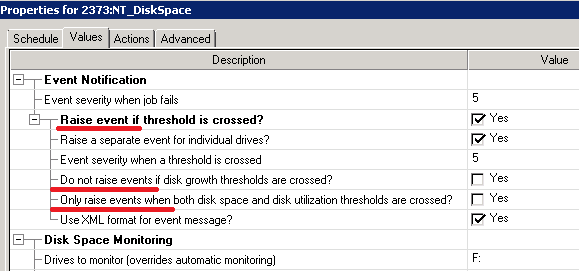

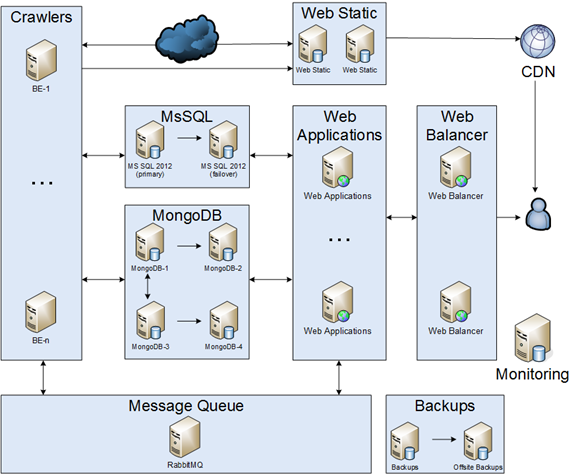
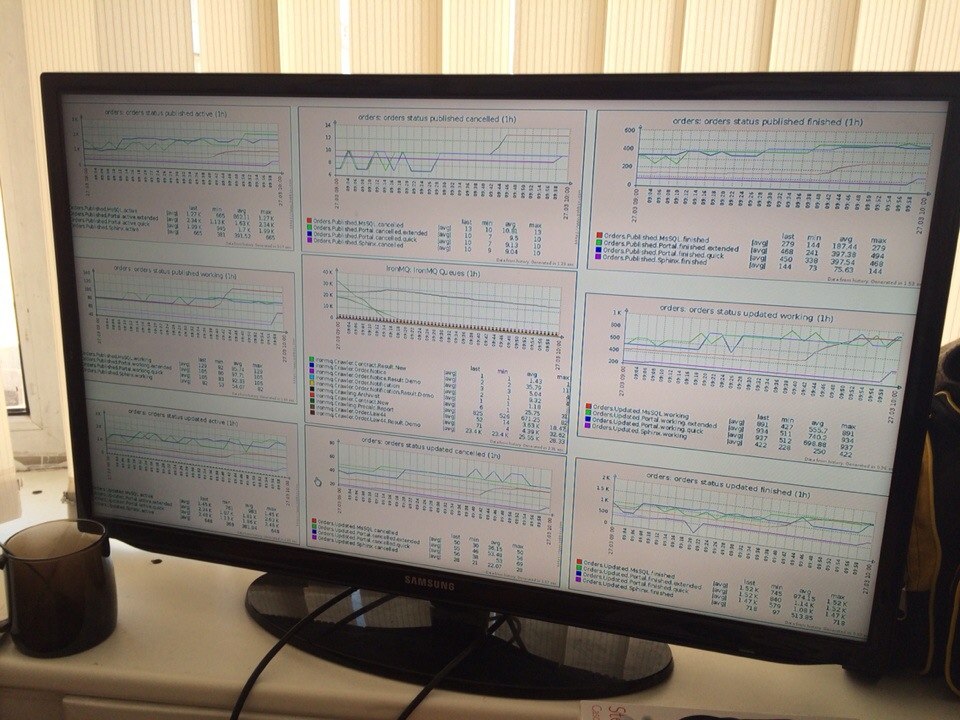


 Today is an important day — after 28 releases of the sixth version we present our PVS-Studio 7.00, in which the key innovation is the support of the Java language. However, during 2018 we have acquired many other important changes related to C++, C#, infrastructure and support of coding standards. Therefore, we bring to your attention a note that sums up the major changes that have happened in PVS-Studio for the last time.
Today is an important day — after 28 releases of the sixth version we present our PVS-Studio 7.00, in which the key innovation is the support of the Java language. However, during 2018 we have acquired many other important changes related to C++, C#, infrastructure and support of coding standards. Therefore, we bring to your attention a note that sums up the major changes that have happened in PVS-Studio for the last time.








